MDR Lite for Microsoft Defender XDR
SERVICE DESCRIPTION
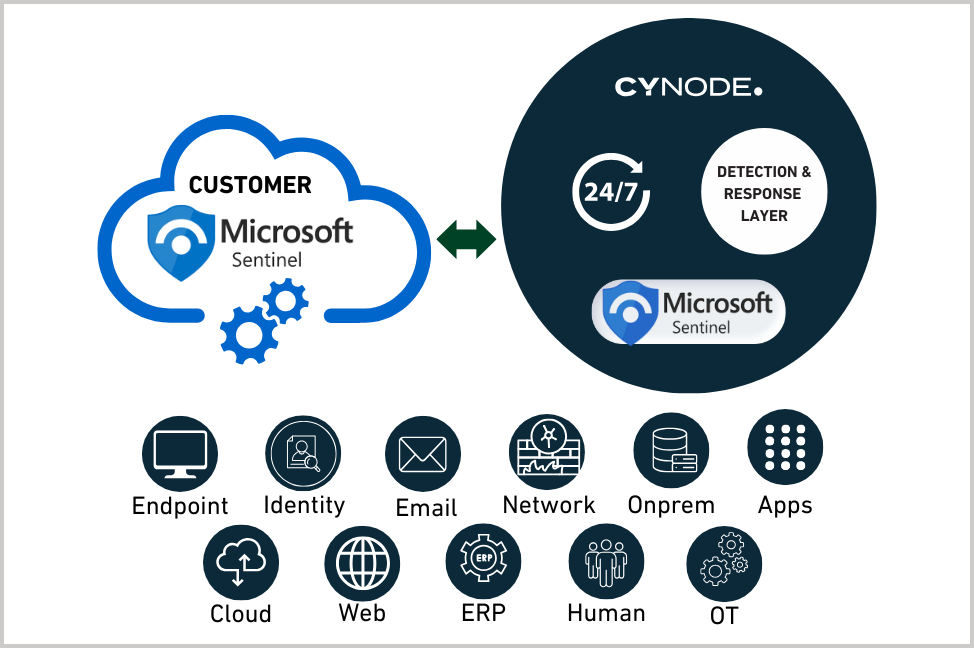
MDR Lite for Microsoft Defender XDR delivers 24/7 monitoring, alert validation, and incident response using Microsoft Sentinel's no-cost security telemetry.
Cynode operates Microsoft-native security operations across endpoint, identity, email/Microsoft 365, cloud, and cloud apps, working in Defender XDR and Sentinel as the system of record.
MDR Lite combines:
- Microsoft AI-driven detections
- Analyst-led triage and investigation
- Advanced hunting and API searches for deeper validation
- SIEM + SOAR operations with Logic Apps automation
WHY IS THIS SERVICE IMPORTANT?
Turning Defender's Capabilities into Cross-Surface Outcomes
Microsoft Defender XDR is strongest when signals are handled as one attack story across multiple surfaces. That requires 24/7 operational ownership to validate signals, correlate activity, and drive consistent response.
MDR Lite delivers that operating model, orchestrating Defender signals across endpoint, identity, email/Microsoft 365, cloud, and cloud apps to detect multi-vector attacks earlier.
By operating on Microsoft Sentinel's no-cost ingestion sources, the service delivers immediate MDR capability at no cost and without platform changes.
How MDR Lite Works
MDR Lite applies Cynode's MDR operating model to Microsoft Defender XDR telemetry through Microsoft Sentinel.
Cynode turns Defender signals into consistent outcomes through:
- AI-assisted correlation across identity, endpoint, email/Microsoft 365, cloud, and SaaS
- Context enrichment (asset, user, incident, and activity context)
- Analyst-led validation and triage
- Advanced hunting and Defender XDR API searches for deeper investigation
MICROSOFT SENTINEL NO-COST INGESTION SOURCES
MDR Lite operates on Microsoft Sentinel ingestion sources that incur no ingestion cost, including:
-
Azure Activity Logs
-
Microsoft Sentinel Health / Service health signals (platform health and operational telemetry)
-
Office 365 Audit Logs (including SharePoint activity, Exchange admin activity, and Microsoft Teams)
-
Security alerts, including alerts from:
-
Microsoft Defender XDR (and its component services such as Endpoint, Identity, Office 365, and Cloud Apps)
-
Microsoft Defender for Cloud
-
RESPONSE ORCHESTRATION
MDR Lite uses Microsoft Logic Apps for prebuilt playbooks covering enrichment, notifications, ticketing, and approved response actions. Automation standardizes response while analysts maintain oversight.
WHO SHOULD USE IT
MDR Lite is ideal for organizations that want to:
-
Run always-on MDR operations on Microsoft Defender XDR
-
Improve cross-surface outcomes across endpoint, identity, email/Microsoft 365, cloud, and SaaS
-
Reduce alert fatigue
-
Standardize response with SOAR playbooks
-
Use Sentinel SIEM without adding ingestion cost
BENEFITS
-
Zero SIEM ingestion cost
-
24/7 SOC coverage
-
Higher alert quality
-
Consistent response execution
-
Immediate operational value from existing Defender XDR investments
PATH TO MDR FOR MICROSOFT DEFENDER XDR
MDR Lite provides a Microsoft-native foundation for Defender XDR operations. Organizations seeking broader visibility and expanded detection can progress to MDR for Microsoft Defender XDR or MDR Core by Cynode.

